Linux环境中Clamav杀毒软件详细使用步骤
【摘要】
1.Clamav介绍
Clam AntiVirus 是一款 UNIX 下开源的 (GPL) 反病毒工具包,专为邮件网关上的电子邮件扫描而设计。该工具包提供了包含灵活且可伸缩的监控程序、命令行扫描程序以及...
1.Clamav介绍
Clam AntiVirus 是一款 UNIX 下开源的 (GPL) 反病毒工具包,专为邮件网关上的电子邮件扫描而设计。该工具包提供了包含灵活且可伸缩的监控程序、命令行扫描程序以及用于自动更新数据库的高级工具在内的大量实用程序。该工具包的核心在于可用于各类场合的反病毒引擎共享库。
主要使用ClamAV开源杀毒引擎检测木马、病毒、恶意软件和其他恶意的威胁
2.部署Clamav杀毒软件
2.1.安装依赖软件
1.安装依赖软件
[root@192_168_81_210 ~]# yum -y install gcc gcc-c++ openssl openssl-devel libcurl-devel
- 1
- 2
- 3
2.2.安装高版本的curl
clamav需要高版本的curl,因此需要进行如下操作
1.安装curl的yum源
[root@192_168_81_210 ~]# rpm -Uvh http://www.city-fan.org/ftp/contrib/yum-repo/rhel7/x86_64/city-fan.org-release-2-1.rhel7.noarch.rpm
2.搜索可用的curl版本
[root@192_168_81_210 ~]# yum --showduplicates list curl --disablerepo="*" --enablerepo="city*"
3.启用yum源
[root@192_168_81_210 ~]# vim /etc/yum.repos.d/city-fan.org.repo
[city-fan.org]
name=city-fan.org repository for Red Hat Enterprise Linux (and clones) $releasever ($basearch)
#baseurl=http://mirror.city-fan.org/ftp/contrib/yum-repo/rhel$releasever/$basearch
mirrorlist=http://mirror.city-fan.org/ftp/contrib/yum-repo/mirrorlist-rhel$releasever
enabled=1 #将enable=0全部改为1
gpgcheck=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-city-fan.org
4.安装curl
[root@192_168_81_210 ~]# yum update curl --enablerepo=city-fan.org -y
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
2.3.安装clamav
1.创建管理用户
[root@192_168_81_210 ~]# groupadd clamav
[root@192_168_81_210 ~]# useradd -g clamav -s /bin/false -c "Clam AntiVirus" clamav
2.编译安装clamav
[root@192_168_81_210 ~]# tar xf clamav-0.102.3.tar.gz -C /usr/local/
[root@192_168_81_210 ~]# cd /usr/local/clamav-0.102.3
[root@192_168_81_210 /usr/local/clamav-0.102.3]# ./configure --prefix=/usr/local/clamav && make && make install
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
2.4.配置clamav
1.创建clamav所在的日志目录和更新病毒库的目录
[root@192_168_81_210 ~]# mkdir /usr/local/clamav/logs -p
[root@192_168_81_210 ~]# mkdir /usr/local/clamav/updata -p
[root@192_168_81_210 ~]# touch /usr/local/clamav/logs/clamd.log
[root@192_168_81_210 ~]# touch /usr/local/clamav/logs/freshclam.log
2.修改目录属性
[root@192_168_81_210 ~]# chown clamav:clamav /usr/local/clamav/logs/clamd.log
[root@192_168_81_210 ~]# chown clamav:clamav /usr/local/clamav/logs/freshclam.log
[root@192_168_81_210 ~]# chown clamav:clamav /usr/local/clamav/updata
3.准备clamav配置文件
[root@192_168_81_210 ~]# cp /usr/local/clamav/etc/clamd.conf.sample /usr/local/clamav/etc/clamd.conf
[root@192_168_81_210 ~]# cp /usr/local/clamav/etc/freshclam.conf.sample /usr/local/clamav/etc/freshclam.conf
4.配置clamav
[root@192_168_81_210 ~]# vim /usr/local/clamav/etc/clamd.conf
#Example //注释掉这一行
#添加以下内容
LogFile /usr/local/clamav/logs/clamd.log
PidFile /usr/local/clamav/updata/clamd.pid
DatabaseDirectory /usr/local/clamav/updata
[root@192_168_81_210 ~]# vim /usr/local/clamav/etc/freshclam.conf
#Example //注释掉这一行
#添加以下内容
DatabaseDirectory /usr/local/clamav/updata
UpdateLogFile /usr/local/clamav/logs/freshclam.log
PidFile /usr/local/clamav/updata/freshclam.pid
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
- 22
- 23
- 24
- 25
- 26
- 27
- 28
- 29
3.更新病毒库
[root@192_168_81_210 ~]# /usr/local/clamav/bin/freshclam
ClamAV update process started at Mon Jan 10 15:33:44 2022
WARNING: Your ClamAV installation is OUTDATED!
WARNING: Local version: 0.102.3 Recommended version: 0.103.4
DON'T PANIC! Read https://www.clamav.net/documents/upgrading-clamav
daily database available for download (remote version: 26417)
Time: 50.0s, ETA: 0.0s [=============================>] 54.84MiB/54.84MiB
Testing database: '/usr/local/clamav/updata/tmp.2d3e0/clamav-916efc430b8ed2604cfb6a9ee168689c.tmp-daily.cvd' ...
Database test passed.
daily.cvd updated (version: 26417, sigs: 1970392, f-level: 90, builder: raynman)
main database available for download (remote version: 62)
Time: 114.0s, ETA: 0.0s [=============================>] 162.58MiB/162.58MiB
Testing database: '/usr/local/clamav/updata/tmp.2d3e0/clamav-7749b161578776d0ca3d108dd9b52726.tmp-main.cvd' ...
Database test passed.
main.cvd updated (version: 62, sigs: 6647427, f-level: 90, builder: sigmgr)
bytecode database available for download (remote version: 333)
Time: 4.4s, ETA: 0.0s [=============================>] 286.79KiB/286.79KiB
Testing database: '/usr/local/clamav/updata/tmp.2d3e0/clamav-f0f2f2da0b8333a43dbc70bcb905c513.tmp-bytecode.cvd' ...
Database test passed.
bytecode.cvd updated (version: 333, sigs: 92, f-level: 63, builder: awillia2)
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
- 11
- 12
- 13
- 14
- 15
- 16
- 17
- 18
- 19
- 20
- 21
4.Clamav常用命令参数
/usr/local/clamav/bin/clamscan --查杀当前目录下的文件
/usr/local/clamav/bin/clamscan -r --查杀当前目录的所有文件及目录
/usr/local/clamav/bin/clamscan dir --查杀dir目录
/usr/local/clamav/bin/clamscan -r dir --查杀目录dir下的所有文件及目录
clamscan -r -i /home --remove -l /var/log/clamscan.log #递归扫描home目录,将病毒文件删除,并且记录日志,将有问题的文件都会进行记录
clamscan -r -i /home --move=/opt/infected -l /var/log/clamscan.log #扫描指定目录,然后将感染文件移动到指定目录,并记录日志
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
5.杀毒扫描报告说明
----------- SCAN SUMMARY -----------
Known viruses: 9141451 #已知病毒
Engine version: 0.102.4 #软件版本
Scanned directories: 498 #扫描目录
Scanned files: 738 #扫描文件
Infected files: 4 #感染文件!!!
Data scanned: 530.25 MB #扫描数据
Data read: 14131.60 MB (ratio 0.04:1) #数据读取
Time: 203.805 sec (3 m 23 s) #扫描用时
- 1
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
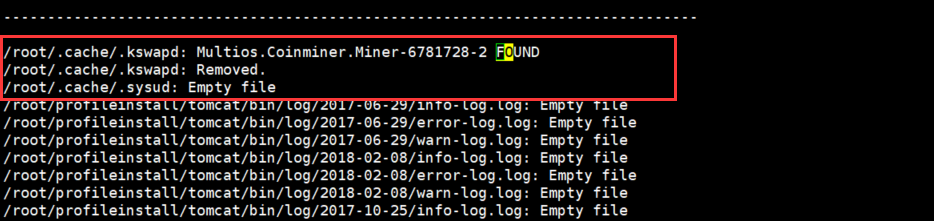
6.病毒文件扫描结果
会在日志中记录一个FOUND字样,并且会将病毒文件删除。
7.设置定时任务
##每天凌晨11点进行文件扫描
crontab -e
0 23 * * * root /usr/local/bin/clamscan.sh
##配置扫描文件
vim /usr/local/clamscan.sh
clamscan -r -i /home --move=/opt/infected -l /var/log/clamscan.log
- 1
- 2
- 3
- 4
- 5
- 6
- 7
文章来源: jiangxl.blog.csdn.net,作者:Jiangxl~,版权归原作者所有,如需转载,请联系作者。
原文链接:jiangxl.blog.csdn.net/article/details/122446768
【版权声明】本文为华为云社区用户转载文章,如果您发现本社区中有涉嫌抄袭的内容,欢迎发送邮件进行举报,并提供相关证据,一经查实,本社区将立刻删除涉嫌侵权内容,举报邮箱:
cloudbbs@huaweicloud.com
- 点赞
- 收藏
- 关注作者


评论(0)